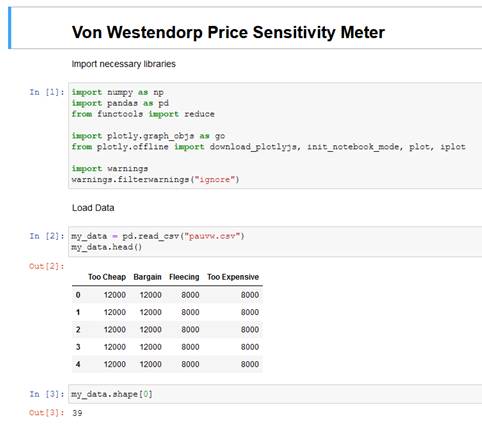
(EFFECT OF BLACKLISTING AND GHOSTING ON YOUR CAREER AND LIFE) - Life Coaching Series
But strange as it may seem, he’s grounded since
the last 2 years and unable to find any meaningful employment. He’s not
outdated or redundant since he has upskilled himself in the recent years, has an
ATS compliant CV and an excellent LI profile. Furthermore, he has a good
network of former colleagues and clients who he can always contact and quote
for any reference check. He’s bemused and dismayed at his present predicament.
He has been applying to several relevant and matching positions online at many
popular jobsites since that has become the norm in the post-covid era. There
have been several occasions when he has encountered the following patterns
explained further.
Note: The above process flow is from the POV of the jobseeker and does not depict the hiring process.
At different stages of the hiring process, he
has experienced something called as “GHOSTING”. A brief snapshot of the
scenarios is listed below as shown in the above diagram:
- a. No further communication after receiving an initial shortlist email from the recruiter
- b.
Recruiter
does not respond to phone calls or emails after the initial screening call
- c.
There
is no interview / meeting link received after it has been scheduled OR recruiter
gives a “NO SHOW” for the pre-scheduled interview
- d.
Recruiter
does not update the status or communicates further process after the interview
- e.
Recruiter
literally acts like a ghost and becomes uncontactable OR passes the buck asking
you to contact someone else in the organization who has no idea about your
status of application
- f.
Recruiter
ditches you at the last minute and conveys a rejection (usually without
justifying any reason) after finalizing terms of the offer
When these similar scenarios keep repeating
over and over again, he gets into action. Being an adept and seasoned
professional, he reviews his digital presence by doing a basic OSINT exercise
on his own online accounts. Here’s the summary of what he finds initially:
- 1. LinkedIn
profile has a social score of 90 and all his data is verified
- 2. Resume
has an ATS score of 84 and all the information is true to the best of his knowledge
- 3. Other
social network profiles do not have any offensive, violent, abusive, sexual, or
objectionable content
- 4. All
his online accounts are secure with 2-step verification enabled
- 5. SEO
ranking of his name and associated identities is also good
- 6. He
doesn’t have any unknown contacts / unverified accounts connected to his social
network
So, he wonders that he is probably amid a “Mid-Life
Crisis” and eventually things will change for the better. But there are questions
that keep haunting him night and day –
i. How will I explain this gap in my
career? Sundry projects / freelancing / part-time work / volunteering are not
going to add up to anything worthwhile!
ii. Why am I going through such a rough
phase? Never been removed or laid-off from any job, never had behaviour or
character questioned, never lied or misrepresented facts, never hidden anything
relevant, never been into any type of criminal activities or misconduct, never
been into any type of political activism or never committed any type of fraud,
then why?
There are many such cases of innocent individuals
whose career and life has been affected by a term called as “BLACKLISTING”.
It is the blackhole of the HR domain that very much exists but is denied by
everyone in the industry. I’m not referring to a plain simple case of
blacklisting of prospective candidates by individual recruiters for genuine or
not-so genuine reasons. That is done by every other company on the planet over
their internal database. What I’m referring to is the maintaining of a very
large database of persons and other entities that is subscribed to by several
large corporates including background screening and verification companies. Such
databases are often stored secretively and shared with select few members
within the HR domain in the corporate world. Prima facie, there shouldn’t be
any problem in doing so since organizations need to keep a tab on who enters
their organization as it is all about brand management and goodwill. The
problem lies in the legitimacy and integrity of the data that is often scoured
from several sources including third party operators, contractors, and
sub-contractors. The moot question is – How reliable are those players and who
owns the accountability for maintaining such a database? Let me clarify that I’m
not referring to data protection laws or right to privacy legislation here at
all. Please note that this is something
maintained privately and is not a government database like “Early Warning
System” (EWS) of the UK or “Global Internet Forum To Counter Terrorism” (GIFCT,
maintained by internet & social media giants) of the US that is referred to
by government agencies or SITA Goods & Passenger Tracking System (S-GPTS, aviation
industry) accessed by most airport authorities worldwide.
A few names that I’m aware of are First
Advantages Esteem, Lexis Nexis, Skynet, World Check Database, Refinitiv World
Check Risk Intelligence, Facebook Secret Blacklist, etc. There are big
corporations that maintain some of this type of database like Thomson Reuters, Stratfor,
Pinkerton Global Intelligence, etc. Once your name / identity gets inserted
into it, a tag / label is attached which can classify you as a “Heightened Risk
Individual” or “Dangerous Person” or similar category for no mistake of yours. The
database need not mention anything to justify the tag or could also contain
falsified information. This is sufficient to deny any opportunity in the
corporate world and even bring you under the radar of various government and /
or private agencies. Further, forget about correction, there is little you can
do to even request access to such data as an individual.
This type of approach can lead to a tragic “comedy
of errors” (compiled from real-life incidents from various sources) as shown
below:
|
Name (changed to protect identity) |
Blacklist Tag |
Actual incident(s) |
|
Mohammed Imran |
Narcotic |
Bought tranquilizers to
manage anxiety / stress without a doctor’s prescription from a local pharmacy |
|
Chruen Cassidy |
Terrorist |
Profusely sweating at an airport
due to stress and physical exhaustion |
|
Disha Saxena |
Lazy & Quarrelsome |
Altercation with local
community members on the issue of hygiene and cleanliness |
|
T. Bala |
Politically Exposed Person |
Tweeting in support of his home government
over a national issue while working overseas |
|
Navneet Singh |
Social misfit |
Unable to communicate
effectively in English in spite being a good software developer |
|
Alex Mayor |
Fraudster |
Defaulter for personal credit
card payment of a miniscule amount |
|
Akash Jain |
Anarchist |
Online search for terms
like “crude bomb”, “anarchy”, etc. to gather general information in order to write
a fiction novel |
One can easily see from the above table that such data can be unverified, biased, outdated, or irrelevant. How names of simple & unsuspecting individuals make it to such kind of databases will be largely unknown, unless thoroughly investigated.
Is it just a complex algorithm or a mean person behind it will remain a mystery until the shadow of the “BLACKGHOST” is exorcized!
So, if you meet with ghosting repeatedly, you
can be sure that your name has been blacklisted. You need to prep-up your act
and perform your own due diligence before it destroys your peace of mind.
Contact the author to know more about identity
management, online reputation management and OSINT.
References:
https://mikesouth.com/free-speech/the-internet-blacklist-database-72337/
https://www.refinitiv.com/en/products/world-check-kyc-screening
https://www.mirror.co.uk/money/revealed-secret-international-blacklist-can-7332879
https://www.theguardian.com/uk/2009/mar/16/blacklisted-workers-hotline
https://insights.dice.com/2019/03/12/exploring-secret-practices-tech-recruiters/
https://forums.studentdoctor.net/threads/pharmacist-blacklisted-on-global-database-esteem.1370449/
https://www.bindmans.com/insight/blog/world-check-database-due-diligence-or-blacklist
https://www.zdnet.com/article/skynet-nsa-terrorist-terminator/